- Business Process Management (BPM)Document Management System (DMS)Electronic Quality Management System (QMS)Risk, Governance & Compliance (GRC)Low Code Rapid Application Development (LC)Business Continuity Management (BCM)Enterprise Architecture (EA)Business Process Management (BPM)Document Management System (DMS)
- Document Control Overview
- AI Content Creation & Improvement
- Policy & Procedure Management (SOP)
- AI Content Mining Parser
- Collaboration & Governance
- Data Migration & Integration
- Interfacing Offline App
 Electronic Quality Management System (QMS)
Electronic Quality Management System (QMS)- Quality Management System Overview
- Document Control & Records Management
- Audit & Accreditation Management
- Corrective & Preventative Action
- Quality Event (Non-conformity / Complaint/ Compliance)
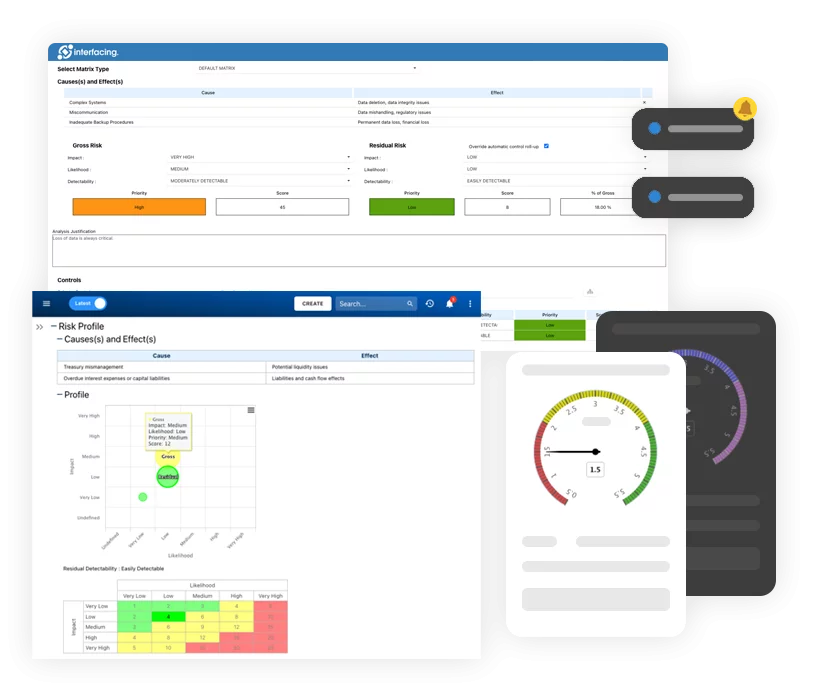
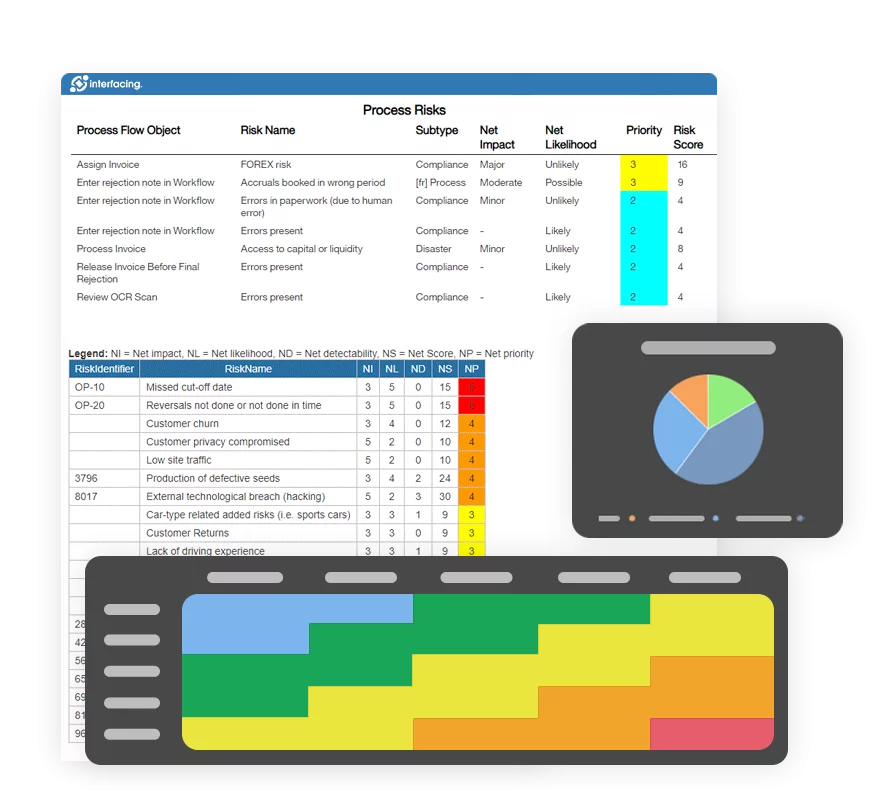
- Risk Management
- Incident Management
- Environmental Health & Safety
- Product & Supplier Management (SCAR)
- Training Management
- Control Management
- Action Items Management
- Management Review
- FMEA
- Pharmacovigilance
- Data Migration & Integration
 Risk, Governance & Compliance (GRC)
Risk, Governance & Compliance (GRC)- Risk, Governance & Compliance Overview
- Risk & Control Management
- Regulatory Compliance
- Collaboration & Governance
- Data Migration & Integration
- Interfacing Offline App
 Low Code Rapid Application Development (LC)
Low Code Rapid Application Development (LC)- Low Code Automation Platform Overview
- Electronic Web Form Design (eFORMS)
- Database Table Entity Designer
- System Integration Designer
- Design & Manage Tasks
- Design & Manage BPMS Apps
- Custom Rules/Guards/Actions
- Electronic Services
- User Homepage
- BAM (Business Activity Monitoring)
- Custom Dashboard Design
- Data Migration & Integration
 Business Continuity Management (BCM)
Business Continuity Management (BCM)- Business Continuity Management Overview
- Business Impact Analysis
- Disaster Recovery Simulation
- Action Item Management
- Mass Notification Management
- Asset Management
- Interfacing Offline App
 Enterprise Architecture (EA)
Enterprise Architecture (EA) - IndustriesRegulatory ComplianceUse CasesLearning CenterFramework & PracticesIndustries
- Healthcare
- Medical Device Technology
- Life Science, Pharmaceutical
- Aerospace & Defense
- Airlines and Aviation
- Media & Telecommunications
- Government and Military
- Technology
- Energy
- Logistics & Port Operations
- Banking & Capital Markets
- Retail & Consumer
- Consulting
- Education
- Engineering & Construction
- Manufacturing
- Financial Services
- Insurance
- Chemicals
Regulatory Compliance- Regulatory Compliance
- ISO
- ISO 9001 (guide)
- ISO 9001:2026 (preparation)
- ISO 17025
- ISO 27000
- ISO 27001
- ISO27002
- ISO 42001
- EU AI Act
- SOC 2 Type 1 & 2
- Sarbanes Oxley
- GxP
- GRC
- Basel
- Digital Signature
- GDPR
- IFRS
- NIST SP 800-53
 Use Cases
Use Cases- Quality Management System (QMS)
- Digital Transformation
- Continuous Improvement
- Governance, Risk & Compliance
- Knowledge Management
- System Deployment (ERP, CRM…)
 Learning CenterFramework & Practices
Learning CenterFramework & Practices - AboutCustomer SuccessPartners

What is
ISO 27001:2022
Please Select contact form.
Definition & Use

ISO 27001:2022 ISMS has been Updated: What’s Changed?
Exploring the ISO 27001:2022 Standard ISMS Framework in Safeguarding Information Security
ISO 27001 explanation: This was developed by the International Organization for Standardization (ISO) for managing information security (a.k.a. Cybersecurity). It helps organizations identify risks and implement information security controls to protect sensitive data. ISO 27001 is widely recognized framework and adopted globally.
ISO 27001:2022 ISMS: This is the updated framework used to establish, implement, operate, monitor, review, maintain, and improve an organization’s information security management system.
Its overarching goal is to create a robust & structured approach to identifying, managing, and mitigating information security risks (risk management protocols).
Understanding ISO 27001:2022 ISMS
ISO 27001 benefits: In today’s digitally driven world, where information is an invaluable asset, protecting sensitive data has become paramount for individuals and organizations alike. Cyber threats, data breaches, and privacy concerns have underscored the need for a robust framework that ensures the security of information assets.
Enter the ISO 27001:2022 ISMS (Information Security Management System) framework – a comprehensive approach to safeguarding information security and mitigating risks. In this blog, we’ll delve into the essence of ISO 27001:2022 ISMS and explore its real-life applications.

The framework is built upon a foundation of core principles & security standards:
Risk Assessment and Management
ISO 27001:2022 ISMS emphasizes the importance of assessing and managing risks that could potentially impact an organization’s information security.
Continuous Improvement
The framework promotes a culture of continuous improvement by encouraging regular review and refinement of the information security management system
Confidentiality, Integrity, and Availability (CIA)
The framework prioritizes maintaining the confidentiality, integrity, and availability of information asset
Legal and Regulatory Compliance
ISO 27001:2022 ISMS ensures that an organization adheres to relevant legal and regulatory requirements related to information security.
Employee Involvement and Awareness
ISO 27001:2022 ISMS encourages involving employees at all levels and ensuring they are aware of their roles and responsibilities in maintaining information security.
Real-World Applications of ISO 27001:2022 ISMS
Example 1: Financial Institutions
Financial institutions handle vast amounts of sensitive customer data, making them prime targets for cyberattacks if there is a lax in cybersecurity protocols. ISO 27001:2022 ISMS offers a structured approach for these institutions to identify vulnerabilities, assess risks, and implement robust security measures. For instance, a leading bank implemented ISO 27001:2022 ISMS to create a secure environment for online banking. By conducting regular risk assessments, the bank identified potential threats and took proactive steps to safeguard customer data. This not only enhanced customer trust but also prevented potential financial losses due to data breaches.
Example 2: Healthcare Sector
The healthcare sector deals with a plethora of confidential patient information. ISO 27001:2022 ISMS plays a crucial role in protecting electronic health records, medical histories, and sensitive research data. A renowned hospital adopted the framework to ensure the security and privacy of patient data. By implementing access controls, encryption protocols, and stringent authentication processes, the hospital reduced the risk of unauthorized access and data leaks. This not only complied with data protection regulations but also preserved the reputation of the institution.
Example 3: E-Commerce Platforms
E-commerce platforms rely heavily on customer trust and secure online transactions. ISO 27001:2022 ISMS aids these platforms in identifying vulnerabilities in their IT infrastructure, ensuring the safe handling of payment information, and maintaining the availability of their services. A prominent e-commerce website integrated the framework to protect customer payment data. By conducting regular penetration tests and security audits, the platform identified and patched vulnerabilities, minimizing the risk of payment fraud and enhancing customer confidence.
Example 4: Manufacturing Industry
The manufacturing industry often grapples with protecting intellectual property, proprietary designs, and production processes. ISO 27001:2022 ISMS offers a structured methodology for identifying potential threats to these valuable assets. A leading manufacturing company adopted the framework to secure its sensitive designs and production data. By implementing strict access controls, employee training programs, and data encryption, the company thwarted attempts at industrial espionage and maintained its competitive edge in the market.
Key Changes in ISO 27001:2022
Embracing a Risk-Driven Approach
Change: ISO 270012022 acknowledges the increasing significance of supply chain risks in information security. It emphasizes the importance of managing risks associated with third-party vendors and service providers.
Impact: Organizations will need to implement measures to assess and manage the information security risks posed by third-party relationships. This may involve conducting due diligence assessments and establishing clear security requirements for vendors.
Contextualizing the ISMS
Change: ISO 27001:2022 introduces the concept of “Context of the Organization,” emphasizing the importance of understanding an organization’s internal and external context to effectively design and implement an ISMS.
Impact: Organizations will need to conduct a thorough analysis of their operational environment, including stakeholder needs, regulatory requirements, and business objectives. This contextual understanding will guide the development and customization of their ISMS to suit their unique circumstances.
Strengthening Leadership Engagement
Change: ISO 27001:2022 underscores the leadership’s role in driving and supporting the ISMS. It places a stronger emphasis on leadership’s commitment, engagement, and accountability in ensuring the success of information security initiatives.
Impact: Senior management will be required to actively champion information security initiatives, allocate resources, and communicate the importance of adhering to the ISMS throughout the organization. This fosters a culture of security from the top down.
Enhanced Communication and Documentation
Change: ISO 27001:2022 introduces requirements for more effective communication within the organization. It emphasizes the need to document and communicate roles, responsibilities, and authorities related to information security.
Impact: Organizations will need to review and enhance their documentation practices to ensure that responsibilities and authorities are clearly defined and communicated. This reduces ambiguity and streamlines decision-making processes.
Addressing Supply Chain Risks
Change: ISO 27001:2022 acknowledges the increasing significance of supply chain risks in information security. It emphasizes the importance of managing risks associated with third-party vendors and service providers.
Impact: Organizations will need to implement measures to assess and manage the information security risks posed by third-party relationships. This may involve conducting due diligence assessments and establishing clear security requirements for vendors.
Incorporating Technology Advances
Change: :ISO 27001:2022 takes into account the rapid technological advancements that have occurred since the previous version. It provides guidance on addressing emerging technologies, such as cloud computing and the Internet of Things (IoT).
Impact: Organizations will need to adapt their ISMS to encompass new technological trends, ensuring that their security measures are aligned with the risks associated with these innovations.
ISO 27001 Certification Process
-
Initiate the Project:
Begin by securing leadership buy-in and forming a dedicated implementation team. Define the scope of your ISMS and identify the key information assets that need protection.
-
Risk Assessment:
Conduct a comprehensive risk assessment to identify potential vulnerabilities, threats, and their potential impacts on your organization’s information security. This step forms the foundation for your risk management strategy.
-
Risk Treatment:
Based on the outcomes of the risk assessment, devise a risk treatment plan. Implement security controls and measures to mitigate identified risks, ensuring that the security posture aligns with your organization’s risk appetite.
-
ISMS Policies and Procedures:
Develop a set of ISMS policies, procedures, and guidelines that outline how information security will be managed within your organization. Ensure that these documents are clear, concise, and aligned with ISO 27001:2022 requirements.
-
Awareness and Training:
Educate your employees about the importance of information security and their roles in maintaining the ISMS. Training programs will empower your workforce to act as the first line of defense against potential threats.
-
Implementing Security Controls:
Deploy the necessary technical and organizational security controls to protect your information assets. This includes access controls, encryption mechanisms, intrusion detection systems, and more.
-
Monitoring and Measurement:
Regularly monitor and measure the effectiveness of your implemented security controls. This involves conducting security audits, vulnerability assessments, and penetration testing to identify potential weaknesses.
-
Review and Continual Improvement:
Gather feedback and insights from your monitoring activities. Conduct regular reviews to assess the performance of your ISMS and identify areas for improvement. Make necessary adjustments to enhance your security posture.
Common Pitfalls in ISO 27001 Implementation
-
Lack of Leadership Support:
Without strong leadership buy-in, your ISMS implementation efforts may face resistance and lack the necessary resources. Ensure that top management is actively involved and committed to the process.
-
Inadequate Risk Assessment:
Rushing through or overlooking the risk assessment phase can lead to incomplete identification of potential threats. A thorough assessment is essential to establish a solid foundation for risk management.
-
Overlooking Employee Training:
Your employees play a critical role in maintaining information security. Neglecting to provide adequate training and awareness programs can leave your organization vulnerable to social engineering and insider threats.
-
Failure to Update Policies:
Information security threats evolve over time. If your ISMS policies and procedures are not regularly updated to address new risks and challenges, they may become ineffective in safeguarding your assets.
-
Ignoring Third-Party Risks:
Many organizations rely on third-party vendors for various services. Failing to assess and manage the security risks posed by these vendors can lead to vulnerabilities in your information supply chain.
-
Insufficient Monitoring and Review:
Without consistent monitoring and review, your ISMS may become outdated and ineffective. Regular audits, assessments, and reviews are essential to ensure your security measures are up to date.
-
Lack of Continuous Improvement:
ISO 27001:2022 ISMS is built on the principle of continuous improvement. Not actively seeking ways to enhance your ISMS and adapt to new threats can result in stagnation and decreased effectiveness.
-
Focusing Solely on Compliance:
While compliance with ISO 27001:2022 is important, treating it as a mere checkbox exercise rather than a holistic security strategy can lead to a false sense of security.
How Interfacing’s Out-Of-Box Solution Assists in Your ISO 27001:2022 Project
With the growing complexity of managing ISO 27001:2022 requirements, organizing information in a central location becomes increasingly important. When an auditor comes to site, they will assess management’s oversight of their third-party service providers as well as the company’s own controls. The majority of thi
Built with a focus on the ISMS framework overview, Interfacing’s Integration Management System (IMS) documentation workflow automation reflects ISO 27001 requirements.
Creating a safe, secure and protected data ecosystem is our commitment to your organization to maintain ISO 27001 compliance.
Key Features of using Interfacing’s Out-Of-The-Box Integrated Management System for ISMS:
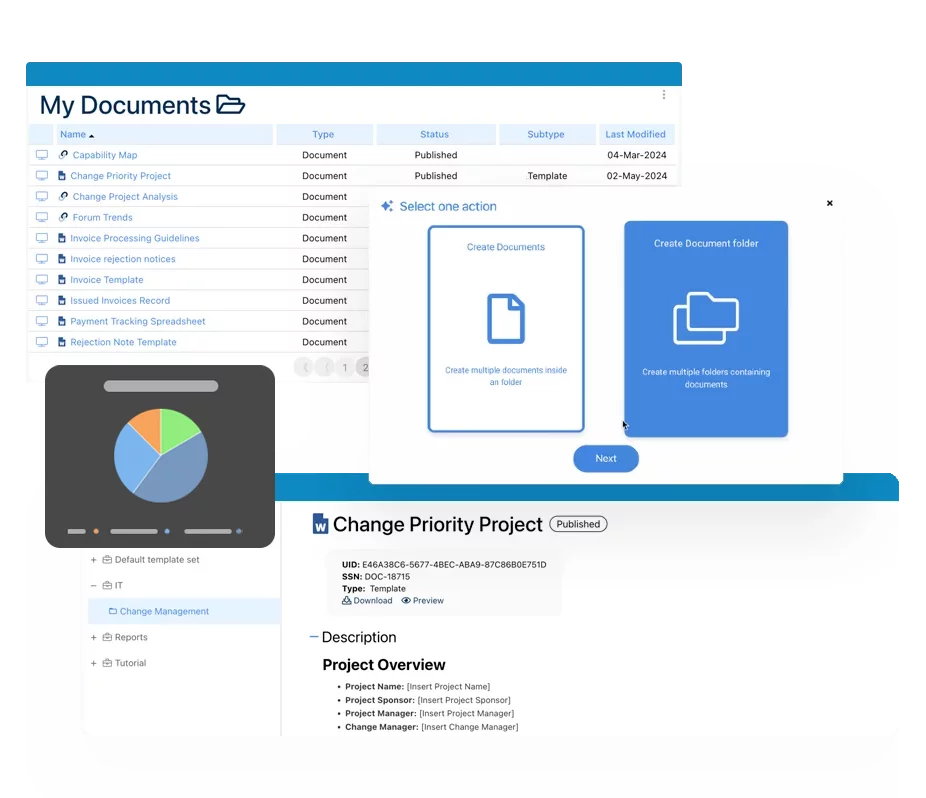
- Pre-built Comprehensive Customizable Library:
- Requirements, Controls, Risks, Processes, Policies, Procedures, Roles & Responsibilities, Capabilities, Assets, ISMS Attributes, etc
- Prebuilt ccentral ISMS Program reporting:
- Statement of applicability, Risk & Control matrix,, Indicator Performance Trend, Improvement Tracking, Audit Non-conformity & action Item status & evidence, etc.
- Ownership, Governance & Approvals on all ISMS objects
- Automated revision scheduled review cycles
- Continuous Improvement & Action Item Automation & Monitoring
- Collaboration & Communication
- Downstream Implementation Impact Visibility & Tracking
- Management Review scheduling & ISMS program consolidated dashboards
- Change & Process/procedure role-based Training assignment & monitoring
Detailed Highlights
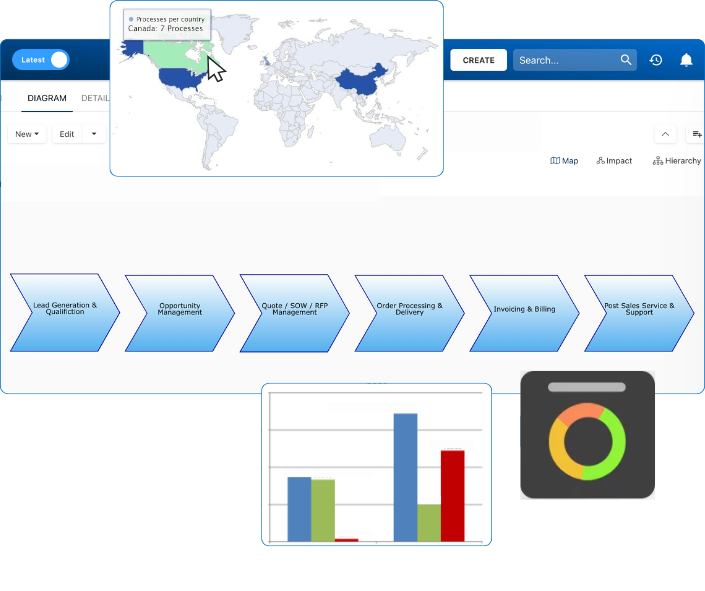
IMS helps organizations streamline and optimize processes, draw interdependencies between processes, resources, roles, rules, risks and controls, and visualize real-time data in an intuitive and user-friendly interface. Monitoring your performance and controlling your information security can be achieved through customized widgets, dashboards and reports embedded in the Integrated Management System platform. Moreover, IMS facilitates implementation of other best practice frameworks, whether they are related or unrelated to ISMS, to support organizations’ continuous improvement management.
IMS empowers organizations to be more proactive when it comes to risk management. It supports a complete risk management lifecycle from risk identification, assessment, prioritization, association of controls and planning mitigations. Our Digital Integrated Management System solution can dynamically visualize risks in different graphs and matrices, generate risk analysis and reports, and facilitate internal and external audit efforts.
An Integrated Management System (IMS) solution, with one common repository, allows employees to access knowledge and share best practices based on roles. Setting different security levels enable organizations to engage all internal and external stakeholders to collaborate on the same processes or tasks without sacrificing information security. Sharing information, raising improvement requests and getting notifications directly within the IMS platform further reduces collaboration frictions, especially for teams located in different locations or using different devices.
Traditional risk management methodology focuses on structure and system rigidness, while Interfacing’s IMS software platform adopts a SaaS model that can be implemented and rolled out in stages. As regulations, laws and policies regarding information security evolve on a daily basis, organizations are obliged to take instant action to attest compliance. IMS helps ISMS absorb and implement changes using an agile approach to accelerate change initiatives and minimize impacts followed by changes.
With integration capabilities with third party systems, Our Integrated Management System solution is capable of creating a single source of truth for your centralized data reference and data lifecycle management. A unified and inclusive Digital Integration platform ensures data ownership, integrity and consistency across departments. Organizing your data in a standardized way in return plays a pivotal role in strengthening your information security.
Leveraging BPM for process optimization and information security controls at the same time proves to be more cost-effective by expanding organizational IT ecosystem. This creates greater value and maximizes ROIs in the long term. Using one solution for various initiatives can also drive synergies across different programs by facilitating monitoring and reporting.
Summary
ISO 27001:2022 ISMS stands as a powerful framework that empowers organizations to take a proactive stance in safeguarding their information assets. Its real-life applications span across various sectors, from finance to healthcare, e-commerce to manufacturing.
Why Choose Interfacing?
With over two decades of AI, Quality, Process, and Compliance software expertise, Interfacing continues to be a leader in the industry. To-date, it has served over 500+ world-class enterprises and management consulting firms from all industries and sectors. We continue to provide digital, cloud & AI solutions that enable organizations to enhance, control and streamline their processes while easing the burden of regulatory compliance and quality management programs.
To explore further or discuss how Interfacing can assist your organization, please complete the form below.

Documentation: Driving Transformation, Governance and Control
• Gain real-time, comprehensive insights into your operations.
• Improve governance, efficiency, and compliance.
• Ensure seamless alignment with regulatory standards.

eQMS: Automating Quality & Compliance Workflows & Reporting
• Simplify quality management with automated workflows and monitoring.
• Streamline CAPA, supplier audits, training and related workflows.
• Turn documentation into actionable insights for Quality 4.0

Low-Code Rapid Application Development: Accelerating Digital Transformation
• Build custom, scalable applications swiftly
• Reducing development time and cost
• Adapt faster and stay agile in the face of
evolving customer and business needs.
AI to Transform your Business!
The AI-powered tools are designed to streamline operations, enhance compliance, and drive sustainable growth. Check out how AI can:
• Respond to employee inquiries
• Transform videos into processes
• Assess regulatory impact & process improvements
• Generate forms, processes, risks, regulations, KPIs & more
• Parse regulatory standards into requirements

Request Free Demo
Document, analyze, improve, digitize and monitor your business processes, risks, regulatory requirements and performance indicators within Interfacing’s Digital Twin integrated management system the Enterprise Process Center®!
Trusted by Customers Worldwide!
More than 400+ world-class enterprises and management consulting firms